This recipe guides you through the configuration of a Singularity container for the Intel® VTune™ Profiler analysis to identify hotspots in an application running in the isolated container environment.
Content expert: Denis Pravdin
Ingredients
This section lists the hardware and software tools used for the performance analysis scenario.
Application: MatrixMultiplication
This Java* application is used as a demo and not available for download.
Tools: Intel VTune Profiler
Note
Starting with the 2020 release, Intel® VTune™ Amplifier has been renamed to Intel® VTune™ Profiler.
Most recipes in the Intel® VTune™ Profiler Performance Analysis Cookbook are flexible. You can apply them to different versions of Intel® VTune™ Profiler. In some cases, minor adjustments may be required.
Get the latest version of Intel® VTune™ Profiler:
From the Intel® VTune™ Profiler product page.
Download the latest standalone package from the Intel® oneAPI standalone components page.
Linux container runtime: singularity
Operating system: Ubuntu* 16.04
CPU: Intel® microarchitecture code named Skylake with 8 logical CPUs
Install and Configure a Singularity* Container
Install the Singularity software (for example, version 2.4.5):
host> VERSION=2.4.5 host> wget https://github.com/singularityware/singularity/releases/download/$VERSION/singularity-$VERSION.tar.gz host> tar xvf singularity-$VERSION.tar.gz host> cd singularity-$VERSION host>./configure --prefix=/usr/local host> make host> sudo make installNote
For detailed installation instructions, see https://singularity.lbl.gov/install-linux.
Create a Singularity container, for example, using the Docker Hub:
host> singularity build ubuntu.img docker://ubuntu:latest Docker image path: index.docker.io/library/ubuntu:latest Cache folder set to /root/.singularity/docker Importing: base Singularity environment Importing: /root/.singularity/docker/sha256:d3938036b19cfa369e1081a6776b07b54be9612bc4c8fed7f139370c8142b79f.tar.gz Importing: /root/.singularity/docker/sha256:a9b30c108bda615dc10e402f62d712f413214ea92c7ec4354cd1cc0f3450bc58.tar.gz Importing: /root/.singularity/docker/sha256:67de21feec183fcd009a5eddc4de8c346ee0f4369a20047f1a302a90716fc741.tar.gz Importing: /root/.singularity/docker/sha256:817da545be2ba4bac8f6b4da584bca0fb4844938ecc462b9feab1001b5df7405.tar.gz Importing: /root/.singularity/docker/sha256:d967c497ce230b63996a7b1fc6ec95b741aea9348118d3328c676f13be789fa7.tar.gz Importing: /root/.singularity/metadata/sha256:c6a9ef4b9995d615851d7786fbc2fe72f72321bee1a87d66919b881a0336525a.tar.gz Building Singularity image... Singularity container built: ubuntu.img Cleaning up...Note
Make sure the ubuntu.img file is created in the current directory.
Run the container.
Singularity allows you to map directories on your host system to directories within your container. This enables read and write data on the host system with ease. For example, if you have a host folder /tmp/vtune with the VTune Profiler and a Java application, you need to run the container and map /tmp/vtune to /local/vtune within the container.
host> singularity shell --bind /tmp/vtune:/local/vtune ./ubuntu.img Singularity: Invoking an interactive shell within container... Singularity ubuntu.img:~>
Run Analysis inside the Container
From the Singularity container, launch the command line interface of the VTune Profiler, amplxe-cl, and run an analysis for your Java application. For example, to run Advanced Hotspots analysis for the MatrixMultiplication application, enter:
Singularity ubuntu.img:~> cd /local/vtune/matrix/
Singularity ubuntu.img:/local/vtune/matrix> /local/vtune/bin64/vtune -collect advanced-hotspots -- /local/vtune/jdk9.0.1-x64/bin/java -cp . MatrixMultiplication 2000 2000 2000 2000Note
To profile a target application running in the Singularity container, make sure to launch the VTune Profiler from the same container. Running the VTune Profiler outside the container for Singularity profiling is not supported.
Advanced Hotspots analysis was integrated into the generic Hotspots analysis starting with VTune Amplifier 2019, and is available via the Hardware Event-based Sampling collection mode.
When the analysis result is collected, you may open it with the GUI version of the VTune Profiler installed on the host system and follow a traditional analysis flow starting with the Summary window that provides an overview of the application performance:
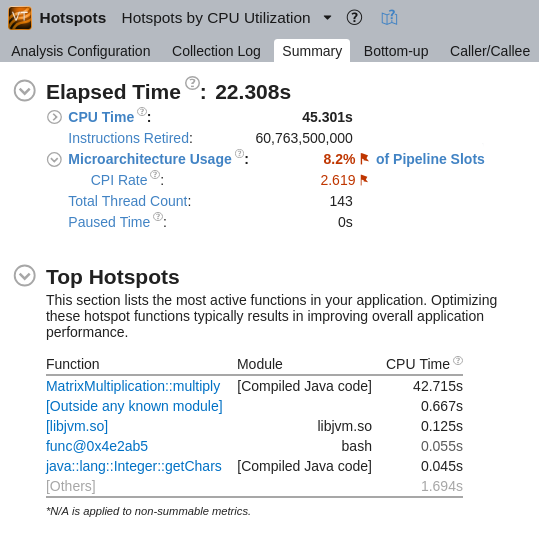
Note
If you need to re-finalize an analysis result outside the Singularity container (for example, in the GUI version of the VTune Profiler installed on the host system), make sure all binary and source files required for module resolution are accessible outside the container.